11. Preliminary Risk Assessment
Summary: A risk assessment is necessary to demonstrate that the processing is not causing a disproportionate impact on data subjects – this assessment describes what could happen to data subjects in case of a data breach, if they are unaware or unable to exercise their rights, if the processing intrudes into their personal sphere, or produces an unfair outcome.
Step 11 aims to systematically identify, assess and address any meaningful potential risks for data subjects, derived from the processing activity. This assessment is required for determining the proportionality of the processing activity, which is necessary to demonstrate that the processing is not causing a disproportional impact to the rights and freedoms of data subjects.
Importantly, the thoroughness of the risk assessment must be proportional to the scope and nature of the processing activity. Larger processing will require a more thorough assessment, while small scale, low risk, common activities will not require such thoroughness.
Keep also in mind that this risk assessment can not be truly meaningfully quantified – neither the severity of damage nor the likelihood of its occurrence. Instead, a reasonable argumentation that supports the conclusion of the risk is expected.
A risk assessment is conducted four times, on each of four different risk scenarios:
- Data breach: What could happen to data subjects if all personal data listed in step 3 is either no longer available (lost/erased), no longer accurate (loss of integrity), or is fully and publicly released (loss of confidentiality)?
- Inability to exercise rights scenario: What could happen to data subjects if they are either unaware that their personal data is processed, they can’t be informed about the process, or their expectations on the processing do not match the actual processing taking place (they are misinformed)? Furthermore, what would happen if they were unable or powerless to exercise their data subject rights? For example, consider that in some processing activities involving observations, it is often not possible to ensure all observed individuals are properly aware and informed. Other processing activities use personal data where it is no longer possible to contact data subjects, or data subjects are no longer able to get in touch with controllers, or even if they are contacted, it is no longer possible to comply with their data access requests.
- Intrusion into secluded/private spaces: Some processing activities require getting in touch with people who may feel it as totally unexpected. Others may require acquiring information in a way that may feel like an intrusion into their personal sphere. This scenario is especially relevant for processing where data was initially collected for other purposes – could this be considered as an unwarranted intrusion, or an interference with their expectation of privacy? For example, processing activities may involve observations in places where individuals could have a reasonable expectation of privacy.
- Inappropriate outcomes: What could happen to data subjects if the processing does not produce a fair outcome? For example, the outcome of the processing is unexpectedly biased or discriminatory, or otherwise harms individuals. This scenario is particularly applicable to processing activities that are meant to produce an outcome affecting data subjects: exam proctoring and scoring, credit worthiness, etc. In other words, what could happen to individuals when something goes wrong with the processing?
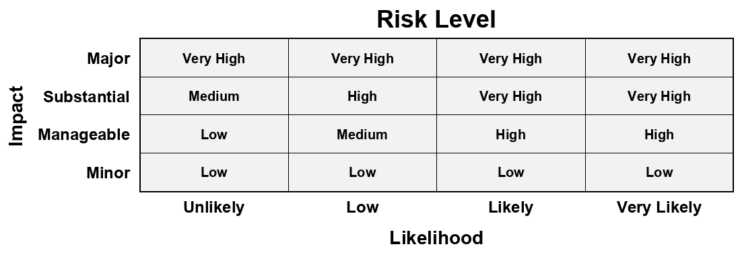
For each one of these risk scenarios, the assessment starts by 1) identifying the nature of the potential damage or damages for data subjects. Then, 2) the potential impact level is assessed, where it is assumed that all implemented organizational and technical safeguards have failed. In other words, what could be the worst that data subjects could experience in this scenario, and how bad would it possibly get? Next, 3) the likelihood that these damages will actually materialize is assessed, taking into consideration all implemented measures and the overall context of the project. Finally, 4) The product of impact versus likelihood thus produces the overall risk level.
Potential damages to consider include:
- Physical damage has an adverse impact to physical integrity, like incorrect data or processing that leads to the wrong medical treatment, or a data breach that abet violent crimes including stalking. Psychological damages can also fall under physical damages, like anxiety, depression, and other psychological damages due to loss of confidentiality or unjustified surveillance.
- Material damage is primarily economic. Examples include career disadvantages (missed recruitment or promotion opportunities, warning letters, job losses, etc.), curtailed state benefits (e.g. unemployment benefits, housing benefits, welfare benefits), discrimination (e.g. when looking for accommodation), identity theft and fraud, extortion based on confidential data, other financial losses, loss of acquired advantages and benefits (e.g. bonus programs, purchased goods or services), unjustified fees or fines, as well as additional expenses in terms of time and money caused by data protection violations (e.g. to unfreeze a bank account or clarify processing errors, including the costs for possible legal advice) and many others..
- Non-material damage has an adverse effect of a social, personal, and legal nature. This category is very diverse. It is therefore helpful to consider four subcategories:
-
- Social disadvantage includes damages to (loss of) reputation and varying degrees of potential humiliation (from embarrassment through loss of face up to serious public humiliation or defamation), mobbing, social discrimination, curtailment of social inclusion for instance through (unjustified) blocking of accounts or incorrect data (e.g. age, being included on exclusion orders).
- Damage to privacy can happen when a person experiences a “creepy” lack of control over their own data and the feeling of being “spied on”, for instance due to video surveillance, biometric recognition, profiling, tracking via websites, end devices and applications or the publication, mention of or reference (e.g. in advertising) to private, intimate details such as address, pregnancy, state of health, sexual or political orientation, religion, etc
- Chilling effects can happen when people refrain from exercising their rights (e.g. to express political opinions) or expressing their personal development (e.g. by visiting certain places) because they fear negative consequences. Chilling effects are a threat above all in the case of data processing operations that constitute unjustified surveillance.
- (Unjustified) interference with rights. Data processing operations may also violate other fundamental rights or result in their violations, e.g. the fundamental right to non-discrimination or freedom of expression. There may be opportunity costs to data subjects caused for not processing data, where the outcomes would be beneficial to data subjects, or it may have an impact on the rights of others (third parties) like the freedom to conduct business or perform scientific research.
Potential impacts are classified as:
Major:
- The damage affects the exercise of fundamental rights and public freedoms (see below), and its consequences are irreversible.
- The consequences are related to special categories of data or to criminal offences, and are irreversible.
- It causes significant social harm, such as discrimination, and is irreversible.
- It affects particularly vulnerable data subjects, especially children, in an irreversible way.
- Causes significant and irreversible moral or material losses.
Substantial:
- The above cases when the effects are reversible.
- Loss of control of the data subject over their personal data, where the extent of the data is high in relation to the amount of data, or the number of individuals involved
- Identity theft of data subjects occurs or may occur.
- Significant financial losses to data subjects may occur.
- Loss of confidentiality of data subject to the duty of professional secrecy or breach of the duty of confidentiality.
- There is a social detriment to data subjects or certain groups of data subjects.
Manageable:
- Very limited loss of control of some personal data and to specific data subjects – other than special category or irreversible criminal offences or convictions.
- Negligible but irreversible financial losses.
- Loss of confidentiality of data subject to professional secrecy, but not of special categories of data, sensitive data or infringement penalties.
Minor:
- The above case, when all effects are reversible.
Potential likelihood are classified as:
Very likely:
- If the risk factor is materialised and not likelihood-dependent.
- Whether there is evidence of several materialisations of this risk in the last year in different entities.
- Whether there is evidence of such a risk materialising in the last year in the same entity.
- There are audits/studies that identify important vulnerabilities in organisational procedures or technical means linked to this risk.
Likely:
- Whether there is evidence of such a risk materialising in the last year in any entity.
- Studies show that the likelihood could be high.
- There are audits/studies that identify possible vulnerabilities in organisational procedures or technical means linked to this risk.
- The elements linked to the risk factors have been implemented with non-mature technologies or organisational procedures, without following quality standards, without being certified by independent third parties.
Low:
- Whether there is evidence of such a risk materialising in the last 10 years in any entity.
Unlikely:
- If there is no evidence of such a risk materialising in any case
Use the table below to estimate the overall risk
Examples: The risk analysis statements below showcase one potential way to explain the risks – Notice the structure of the example, where it starts by stating the particular scenario and identify potential damages. This is followed by an assessment of the impact level, then an estimation of the likelihood. After this discussion, an overall estimation is then given. Keep in mind that the examples below are rather short, as they are meant to provide an example of the structure of the reasoning. For the assessment of actual processing activities, a more thorough discussion is likely needed, depending on the scope of the processing activity – as explained above.
Data breach: Considering the categories of personal data described in table 3, in the event of a data breach, some data subjects may experience non-material damage such as embarrassment (if they believe that their survey questions are of a controversial or unpopular nature). As collected personal data is not considered to be of a sensitive nature, we can reasonably expect this damage to have a manageable impact on them, as they will only experience limited (albeit irreversible) loss of control of their personal data. Given the safeguards already described elsewhere in this privacy scan, and that a data breach has not materialized so far, we can reasonably estimate that the risk level is low.
Inability to exercise rights: Considering that for the observation activities described above, it is quite possible that some of the observed individuals will not be aware of the observation taking place, it is very likely that they will not be able to exercise their data protection rights. However, considering the safeguards described above, the fact that all information derived from observations will not be linked to data subjects individually, and that all observations take place once (or a very few times) in a public setting where data subjects are already aware that their actions are observed by others, and already behave accordingly, we can reasonably estimate that the impact of any potential damage on data subjects will be minor. Therefore, we can reasonably estimate that the risk level is low.
Intrusion into secluded/private spaces: As described in step 2, we will collect contact information from the website of the data subject’s organizations, and will email them directly the invitation to participate in the project. As a result, some data subjects may be surprised by this, or may experience some annoyance. Still, we can reasonably assume that the impact on data subjects from this intrusion to be manageable. In addition, because our targeting is limited to data subjects who, due to their professional profile, are already experts on the topic of the project, the likelihood that they would consider receiving this invitation as overly intrusive is likely to be low. Therefore, we can reasonably estimate that the risk level is medium.
Inappropriate outcome: As the processing activities of this research project are not intended to have any impact on data subjects individually – as data subjects do not expect the project results to have any impact on them individually – we can reasonably expect that there will not be any significant risks of an inappropriate outcome on data subjects
Previous: Obtaining, Consulting, and Dealing with Data Subjects’ Views of the Processing
- Description of the Project’s Purpose
- Description of Data Subjects
- Description of the Categories and Purposes of Personal Data
- Description of the Processing of Personal Data
- Description of Information Provided to Data Subjects
- Description of How Data Subjects Can Exercise Their Data Subject Rights
- Description of Lawful Basis for Processing
- Description of Measures to Ensure Compliance By Processors and/or Joint Controllers
- Description of Planned Transfers of Personal Data to Other Countries Outside the EU
- Obtaining, Consulting, and Dealing with Data Subjects’ Views of the Processing
- Preliminary Risk Assessment