11. Preliminary Risk Assessment
The goal of this step is to balance the expectations and intentions of the controller with the consequences of the actual implementation of the processing for the data subjects. This is achieved by conducting a preliminary risk assessment, that is meant to identify and anticipate possible adverse or unintended effects – damages – that the processing might have on data subjects, and to describe the (legal, technical and organizational) safeguards that will manage (reduce / mitigate, avoid / eliminate or accept / assume) these potential risks.
A risk to rights and freedoms of data subjects (damages) can be presumed if the processing is likely to result in physical, material, or non-material damages to natural persons.
- Physical damages have an adverse impact to physical integrity, like incorrect data or processing that leads to the wrong medical treatment, or a data breach that abet violent crimes including stalking. Psychological damages can also fall under physical damages, like anxiety, depression, and other psychological damages due to loss of confidentiality or unjustified surveillance.
- Material damages are primarily economic. There are many conceivable economic damages that can be triggered by data protection violations. Examples include career disadvantages (illegitimate performance and behavioural control, missed recruitment or promotion opportunities, warning letters, job losses, etc.), curtailed state benefits (e.g. unemployment benefits, housing benefits, welfare benefits), discrimination (e.g. when looking for accommodation), identity theft and fraud, extortion based on confidential data, other financial losses, loss or falsification of evidence (e.g. in a court case or in the context of having to prove that services were provided in a work context), loss of acquired advantages and benefits (e.g. bonus programs, purchased goods or services), unjustified fees or fines, as well as additional expenses in terms of time and money caused by data protection violations (e.g. to unfreeze a bank account or clarify processing errors, including the costs for possible legal advice) and many others.
- Non-material damages have an adverse effect of a social, personal, and legal nature. This category is very diverse. It is therefore helpful to use four subcategories:
- Social disadvantages include damages to (loss of) reputation and varying degrees of potential humiliation (from embarrassment through loss of face up to serious public humiliation or defamation), mobbing, social discrimination, curtailment of social inclusion for instance through (unjustified) blocking of accounts or incorrect data (e.g. age, being included on exclusion orders).
- Damage to privacy can happen when a person experiences a “creepy” lack of control over their own data and the feeling of being “spied on”, for instance due to video surveillance, biometric recognition, profiling, tracking via websites, end devices and applications or the publication, mention of or reference (e.g. in advertising) to private, intimate details such as address, pregnancy, state of health, sexual or political orientation, religion, etc.
- Chilling effects can happen when people refrain from exercising their rights (e.g. to express political opinions) or expressing their personal development (e.g. by visiting certain places) because they fear negative consequences. Chilling effects are a threat above all in the case of data processing operations that constitute unjustified surveillance.
- (Unjustified) interference with rights. Data processing operations may also violate other fundamental rights or result in their violations, e.g. the fundamental right to non-discrimination or freedom of expression (see below). There may be opportunity costs to data subjects caused for not processing data, where the outcomes would be beneficial to data subjects, or it may have an impact on the rights of others (third parties) like the freedom to conduct business or perform scientific research.
What are these (other) fundamental rights of individuals?
The fundamental rights are listed in the Charter of fundamental rights of the European Union. It includes, among others:
- The right to equality and non-discrimination
- The right to life and physical integrity
- Religious freedom
- Personal freedom
- Personal and family privacy and self-image
- Freedom of expression and information
- Academic freedom
- Freedom of assembly
- Freedom of association
- Right to education
- Freedom to conduct a business
- Free access to public positions and functions in conditions of equality
- Effective judicial protection
- Freedom of assembly and of association in trade union membership and the right to petition.
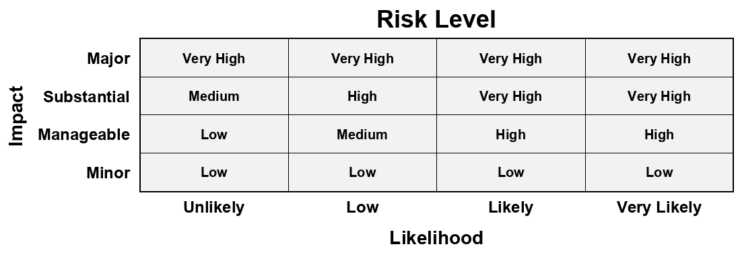
Risk assessment has two dimensions: first, the impact of the damage, and second, the likelihood that the event and the resulting damages occur. You can use a four-tier scale to classify the damage impact and its likelihood:
Damage impact:
- Major:
- The damage affects the exercise of fundamental rights and public freedoms (see below), and its consequences are irreversible.
- The consequences are related to special categories of data or to criminal offences, and are irreversible.
- It causes significant social harm, such as discrimination, and is irreversible.
- It affects particularly vulnerable data subjects, especially children, in an irreversible way.
- Causes significant and irreversible moral or material losses.
- Substantial:
- The above cases when the effects are reversible.
- Loss of control of the data subject over their personal data, where the extent of the data is high in relation to the amount of data, or the number of individuals involved
- Identity theft of data subjects occurs or may occur.
- Significant financial losses to data subjects may occur.
- Loss of confidentiality of data subject to the duty of professional secrecy or breach of the duty of confidentiality.
- There is a social detriment to data subjects or certain groups of data subjects.
- Manageable:
- Very limited loss of control of some personal data and to specific data subjects – other than special category or irreversible criminal offences or convictions.
- Negligible but irreversible financial losses.
- Loss of confidentiality of data subject to professional secrecy, but not of special categories of data, sensitive data or infringement penalties.
- Minor:
- The above case, when all effects are reversible.
Likelihood of the damage:
- Very likely:
- If the risk factor is materialised and not likelihood-dependent.
- Whether there is evidence of several materialisations of this risk in the last year in different entities.
- Whether there is evidence of such a risk materialising in the last year in the same entity.
- There are audits/studies that identify important vulnerabilities in organisational procedures or technical means linked to this risk.
- Likely:
- Whether there is evidence of such a risk materialising in the last year in any entity.
- Studies show that the likelihood could be high.
- There are audits/studies that identify possible vulnerabilities in organisational procedures or technical means linked to this risk.
- The elements linked to the risk factors have been implemented with non-mature technologies or organisational procedures, without following quality standards, without being certified by independent third parties.
- Low:
- Whether there is evidence of such a risk materialising in the last 10 years in any entity.
- Unlikely:
- If there is no evidence of such a risk materialising in any case
Possibility versus Probability
Although it’s often useful to think about all the possibilities that exist, decisions generally are better served by focusing on probabilities…or at the very least probabilities must be part of the deliberation.
It’s really only when we start talking about probabilities that we have useful information. That is when we move from having to worry about everything to having a more manageable list of concerns. It is useful to think of what events are possible, but only as a means of surfacing events on which to analyse probability. Decisions should be informed by probabilities.
Potential risk scenarios to consider
To proceed in a systematic manner with this preliminary risk assessment, you should consider these potential risk scenarios:
- Data breach scenario:
Data Security is one of the principles of the GDPR. Controllers shall implement appropriate technical and organisational measures to ensure the ongoing confidentiality, integrity, availability and resilience of processing systems and services. The risk of adverse impacts on data subjects stemming from a data breach of personal data, or related security incident, needs to be assessed. The goal is to ensure processed personal data is adequately secured.
For each item listed in step 3, you should describe the potential damages that a data breach could produce. Next, you should describe the implemented measures/safeguards (described elsewhere in the privacy scan) that reduce the impact and/or likelihood of that damage. Then, considering potential damages and implemented safeguards, you should assess the overall risk of the data breach – low, medium, high or very high.
- Inability to Exercise Rights scenario:
This element links to the concept that data protection begins with the individual’s ability to control the data that pertains to him or her, by exercising their data subject rights. Individuals cannot exercise their rights when there are procedural or transparency shortcomings. Those shortcomings may range from websites that are not use friendly to information sheets that are either too dense, too incomplete or both. The goal is to ensure that Individuals can easily exercise their rights, for example by implementing sufficient measures and safeguards that ensure individuals are properly informed, and are able to exercise their data protection rights in an adequate manner.
Considering the nature of the processing, you should describe potential damages that could arise when individuals are not adequately informed about the processing of their personal data, or if they are powerless to object or otherwise influence it. Next, you should describe the implemented measures/safeguards that reduce the impact and/or likelihood of that damage. Then, considering potential damage and implemented safeguards, you should assess the overall risk of the discussed scenario – low, medium, high or very high.
- Intrusion into Secluded Spaces:
The respect for private and family life states: “Everyone has the right to respect for his or her private and family life, home and communications.” Observation should not take place where there is an expectation of being in a private space. Where observation is necessary, the observed data must be used only for purposes that a reasonable person would see as being in context. There should be no secret observation. People may stifle their behaviors or thoughts because of excessive observation. Examples include inappropriate intrusion into secluded (private) space, Disruption and intrusion from unwanted or unexpected (commercial) communications or contacts, loss of control over private spaces.
Considering the nature of the processing, you should describe potential damage that could arise from the intrusion into individuals’ secluded spaces. Next, you should describe the implemented measures/safeguards that reduce the impact and/or likelihood of that damage. Then, considering potential damage and implemented safeguards, you should assess the overall risk of the discussed scenario – low, medium, high or very high.
- Inappropriate Outcomes to People:
The GDPR requires fairness, which includes fair outcomes. Controllers are expected to recognize, mitigate, and /or minimize inappropriate outcomes to people (data subjects and any other third party) and should demonstrably contribute to trusted (digital) innovation. This expectation includes the impact on opportunity costs on people for not processing data, where the processing outcomes would’ve been beneficial to people.
Examples include inappropriate bias, inappropriate discrimination, or harm derived from biased or inappropriate decisions related to civil, consumer or patient rights. People may not receive the tangible benefits of data driven insights because of data use reticence, like credit or employment denial caused by bias; less than optimal health outcomes from insights that were not pursued; diminished access to key services or loss of liberty.
Considering the nature of the processing, you should describe potential damages – inappropriate outcomes to people – that could arise if the processing takes place, and what could happen if it doesn’t take place, could that bring a significant disruption to someone’s education or research project? Next, you should describe the implemented measures/safeguards that reduce the impact and/or likelihood of that damage. Then, considering potential damage and implemented safeguards, you should assess the overall risk of the discussed scenario – low, medium, high or very high.
If this preliminary risk assessment identifies the possibility of a high risk of damages to data subjects, or if the processing is included in the list of processing operations considered to carry a high risk, you should notify the faculty privacy officer, who will upgrade this privacy scan into a Data Protection Impact Assessment (DPIA).
When this preliminary risk assessment indicates that there is a likelihood of high risk in processing operations, it is necessary to take actions that will be focused on reducing the risk to an acceptable medium or low risk level.
These actions will often require a more in-depth systematic description of processing (if the one provided in the privacy scan is found to be insufficient), which may lead to the identification of additional risk-reduction measures.
Importantly, updating to a DPIA requires conducting a more thorough assessment of necessity and proportionality, using these three criteria:
- Judgement of suitability: It must be determined whether the processing is fit for purpose. Processing responds to certain objective deficiencies, demands, requirements, obligations or opportunities and can meet the following purposes proposed with sufficient effectiveness.
- Judgement of necessity: It must be determined whether the intended purpose cannot be achieved in another less harmful or invasive way, i.e. there is no alternative processing that is equally effective in achieving the intended purpose.
- Judgement of proportionality in the strict sense: The seriousness of the risk to rights and freedoms, and its intrusion into privacy, must be appropriate to the aim pursued and proportionate to the urgency and severity of the processing. The benefit that the processing provides to society has to be weighed against the impact on other fundamental rights – from a data protection point of view: “The processing of personal data should be designed to serve mankind.. The right to the protection of personal data is not an absolute right; it must be considered in relation to its function in society and be balanced against other fundamental rights, in accordance with the principle of proportionality…” (Recital 4 GDPR).
This assessment should result in a decision whether or not to carry out the processing or, if necessary, to modify it so that it complies with the three required judgements.
This assessment will require the involvement and advice of the UU DPO (Data Protection Officer), who will monitor the performance of the DPIA. Depending on the nature of the processing operations, the involvement of other stakeholders may also be required. For example, the UU and/or the Geo faculty board, the UU CISO (Chief Information Security Officer), other non-UU controllers, data processors, external advisors and/or consultants.
When a DPIA has indicated that the processing operation is required or has been assessed as appropriate, or desirable, but it still found that the residual risk of such processing could still endanger the rights and freedoms of data subjects, the Data Protection Supervisory Authority (the AP in the Netherlands) should be consulted.
Previous: Obtaining, Consulting, and Dealing with Data Subjects’ Views of the Processing
- Description of the Project’s Purpose
- Description of Data Subjects
- Description of the Categories and Purposes of Personal Data
- Description of the Processing of Personal Data
- Description of Information Provided to Data Subjects
- Description of How Data Subjects Can Exercise Their Data Subject Rights
- Description of Lawful Basis for Processing
- Description of Measures to Ensure Compliance By Processors and/or Joint Controllers
- Description of Planned Transfers of Personal Data to Other Countries Outside the EU
- Obtaining, Consulting, and Dealing with Data Subjects’ Views of the Processing
- Preliminary Risk Assessment